Agentic AI is transforming how security teams operate. As an early partner, you’ll help shape how tomorrow’s risk mitigation is built.
Use our World's First Technology.
Collaborate with our team to solve your challenges
Extend your Cyber Threat Intelligence (CTI) team with always-on AI agents - delivering 15x mean time to investigate,
30% reduced operating costs, and scalability for tomorrow’s threats.









%20Gaps%20Are%20Costing%20You.png)

Protos AI is your force multiplier — AI agents that reason and think like a junior analyst — helping you move from data wrangling to faster, higher-quality decisions across cyber, financial crime, and risk investigations.
.png)
Integrate feeds, unstructured data sources, and applications using Protos AI’s ready-made connectors. For custom data sources, Protos Labs team will create a connector for you.
You define the objective. Protos AI autonomously carries out collection, analysis, and synthesis across connected tools — following the same investigative workflow as a human analyst
Protos AI delivers decision-ready intelligence outputs for review and action, with your feedback continuously refining future investigations. Beyond reports, Protos AI can also integrate with downstream tools for action.


Our AI agent serves as a junior cyber threat intelligence analyst — delivering across core CTI use cases, autonomously and at scale.

Autonomously enrich new indicators, map related MITRE ATT&CK techniques, and analyze supporting infrastructure in minutes — eliminating manual lookups and accelerating first‑cut threat analysis so teams can act faster with confidence.

Continuously monitor vendors for any active targeting or mentions.

Identify CVEs from latest threat advisories and identify potentially impacted assets within my organizations.

Analyze large scale logs for IOCs from newly published threat reports to check if your organization was previously compromised.

Identify linkages between disparate malware or phishing incidents

Automatically correlate logs and alerts across multiple security tools to build a clear, end-to-end timeline of an attacker’s activity — without manually switching consoles or stitching formats. Save hours typically spent piecing together scattered data to understand what happened, when, and how.


Our AI agent serves as a junior investigation analyst — delivering use cases across cyber insurance, financial crime, trade compliance and risk intelligence.

Cross-validate data from proposal forms, underwriting guidelines and attack surface scans for better risk decisions.

Scan your insurance portfolio to detect exposure to a new vulnerability. What took days, now takes minutes.

Reduce false positives and investigation time by prioritising alerts and cases based on behavioural risk, materiality, and context.

Identify emerging fraud patterns and control gaps by analysing confirmed fraud cases, transaction behaviour, and investigation outcomes.

Improve sanctions and export control decisions by contextualising counterparties, transactions, and jurisdictions to focus reviews on true compliance risk.

Accelerate onboarding and periodic reviews by synthesising customer data, adverse media, and ownership structures into clear, defensible risk assessments.
Show easily measurable outcomes without relying on overly complicated models.

Cost Saving

Faster
.png)
Utilization
.png)
Improvement
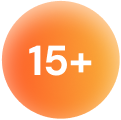



.webp)

Comparison: Traditional vs. AI Augmented
.svg)
1. Feed: Assume OSINT only for comparison.
2. TIP (License + Hosting): $200,000
3. Enrichment tools: $30,000
3. Analyst: 2 FTE for redundancy: $250,000
.svg)
1. Feeds: Assume OSINT only for comparison.
2. TIP: No longer needed.
3. Analyst: 1 FTE + Unlimited AI agents.


In a world full of "agentic" claims, we stand apart.
Protos AI is engineered for superior performance, unparalleled adaptability and high levels of accountability.





Agentic AI is transforming how security teams operate. As an early partner, you’ll help shape how tomorrow’s risk mitigation is built.